OWASP Top 10 Security Vulnerabilities
Adherence with OWASP can help make applications more resistant to cyber threats and dramatically improve cyber resilience.
The Open Web Application Security Project (OWASP) is a standard awareness document for developers and web application security. It represents a broad consensus about the most critical security risks to web applications. It’s an international security standard used by organizations all over the globe.
OWASP History and Testing.
It was launched in 2001 and became a nonprofit in 2004 to improve the security of applications notably web apps. OWASP is a standard awareness documentary that represents a critical security risk to web apps. Most of the stakeholders of the project are volunteers who aren’t affiliated with any tech group. It fuses a community of open-source projects with over 1000 members and more than a thousand chapters, before complying with their list of top 10 risks. The data and docs are located in a GitHub repository managed by OWASP. They also take surveys from industry experts, when data is collected, analyzed and reviewed and a top list of recurring risks is ranked with 8 risks from the repo data and 2 from the survey. All the editing process is recorded on GitHub and a public consensus is reached before the top 10 list is released.
Top 10 Web Application Security Risks
The new list was released on 24 September 2021. It always features different changes in category order and category names. There are three new categories, four categories with naming and scoping changes, and some consolidation in the Top 10 for 2021. The categories are ranked on 3 major plots: exploitability, likelihood and technical impact
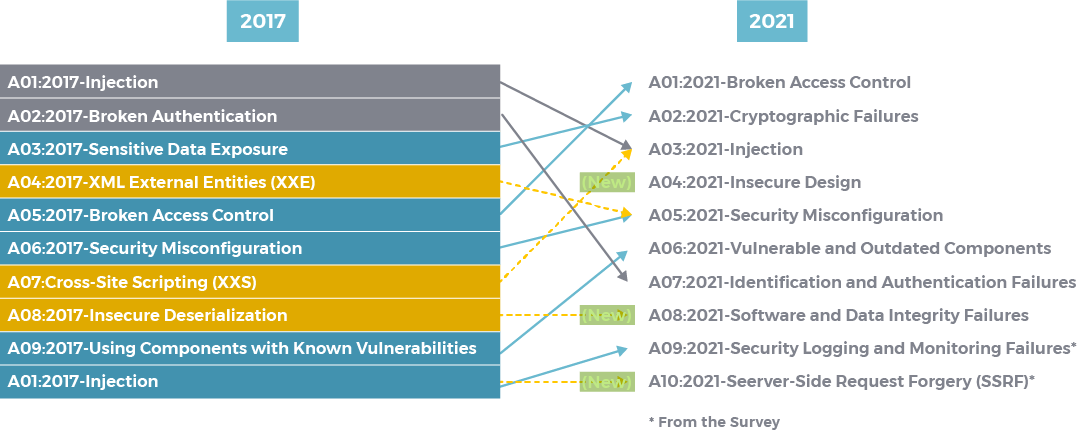
Broken Access Control
It has the top spot in 2021. It is infamously called the holy grail of the OWASP. It is seen largely as the most popular form of risk created by cybercriminals. It bypasses authorization safeguards and performs tasks like authorized users. It gives attackers access to sensitive data, and performs modifications or destroys the data.
Cryptographic Failures
Formerly known as sensitive data failure in OWASP 2017. It’s seen by OWASP as a failure of secure data transfer. this category exploits info transferred when secured information is transferred between 2 people. it provides useful post-exploit info and it involves advanced persistent threats.
Injection
This exploits a vulnerable computer by introducing malicious code to web apps which changes the way the program executes. For example, by injecting this code into web apps an attacker can steal authenticated cookies and use them on other online services and trick these services into thinking that the identity is from a legitimate source. It consists of SQL injection, NoSQL, and LDAP injection. untrusted data is sent to an interpreter as part of a command or query.
Insecure Design
A new category was introduced in 2021. It was included to raise awareness for developers to include more security patterns and principles from design. It’s included to show how important it’s when new apps are introduced in a network infrastructure especially given the supply chain attack on SolarWinds and the effects it had on 3rd party service providers.
Security Misconfiguration
It was present in 90% of web apps that were tested for the research. It’s a failure to implement all the sec controls for a server or web app the incorrect implementation of the sec controls. the risk often occurs through human errors which could include misconfiguring errors on the sec of the apps, not changing default login credentials, lack of computer skills or pressure to deliver quickly on projects.
Vulnerable and Outdated Components
Formerly known as using components with known vulnerabilities. this cat includes an operating system, web or app server, DBMS, APIS, components runtime environment and libraries that are vuln or out of date. attackers just need to find vulnerable and outdated components to compromise a system. it’s an ongoing process because approximately there are over 18000 vulnerable discovered every year.
Identification and Authentication Failure
Formerly known as broken authentication. this is an attack that has seen a reduction in occurrence. It comprises passwords, keys session tokens and user info to assume the privilege of a legitimate user. the use of Multi-Factor Authentication(MFA) can help to protect sensitive information for users
Software and Data Integrity Failure
It’s also a new cat in 2021. it focuses on CI/CD pipelines. software updates and includes insecure deserialization. it relates to codes and infrastructure that don’t protect against integrity violations. For example, the use of untrusted app plugins can lead to access to your apps.
Security Logging & Monitoring Failures
It’s hard to test for due to a lack of CVE data. Insufficient logging and monitoring, coupled with missing or ineffective integration with incident response, allows attackers to further attack systems, maintain persistence, pivot to more systems, and tamper, extract, or destroy data. Failures in this category can seriously impact visibility, incident alerting, and forensics.
Server-Side Request Forgery (SSRF)
It’s the no 1 risk that was recorded from the community survey. Server-Side Request Forgery flaws occur whenever a web application fetches a remote resource without validating the user-supplied URL. The attacker abuses the server functionality causing it to access and manipulate inaccessible info that isn’t accessible to the attacker.
Conclusion
Developers, owners and users of web apps should know of this threat especially when it is the web apps that are e-commerce or touching a database over the internet. this helps you proffer proactive solutions from a defensive path rather than defensive. Adherence with OWASP can help make applications more resistant to cyber threats and dramatically improve cyber resilience.

