Uber internal system breach by teenage hacker
The attacker was carried out with MFA Fatigue Attack - which is the tireless spamming of 2FA notification
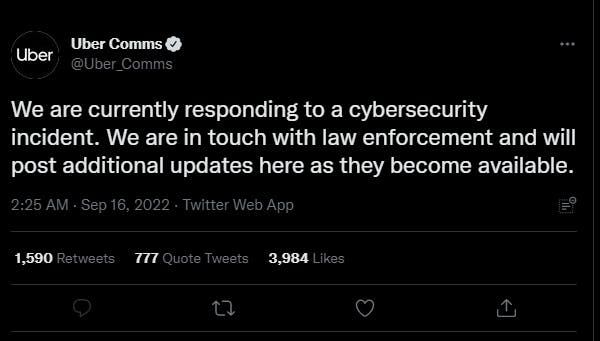
Why bother with expensive and complex zero-day exploits when there are much easier ways to bypass a company security system. This was the case when Uber announced On Friday 16 September 2022 by 2:25am via their PR Twitter account that they were hacked.
Uber a Ride-Hailing company, that offers mobility as a service and holds data of millions of users has been breached. The attack allegedly is said to be carried out by an 18-year-old and was majorly based on social Engineering.
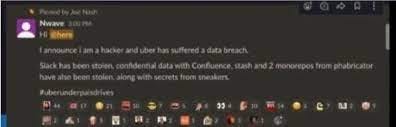
Uber employees on Thursday 15 September by 3pm received a strange yet dreaded message on the company’s slack channel.
"I announce I am a hacker and Uber has suffered a data breach."
This devastating attack by the intruder is one of the infamous attack because as popularly said in information security
there’s no patch to human stupidity.
This attack is quite different from regular security compromise we see which identify with ransomware, espionage and extortions. He wasn’t interested in causing a havoc but just for fun as he used the #uberunderpaysdriver. Lot of researchers and new outlets have reported this to be some sort of hacktivism.
The story behind the breach:
The teenage attacker somehow obtained an Uber employees WhatsApp phone number, he then directed the employee to a fake Uber login page through phishing, where he was able to dump the employee credentials and log in the genuine site. Though Uber like many companies and services uses the security feature of Multi Factor Authentication (MFA). The employee password wasn’t enough to grant access to the Uber internal system. The attacker then carried out an MFA Fatigue Attack - which is the tireless spamming of 2FA notification at someone until they become fatigued and just accept the request.
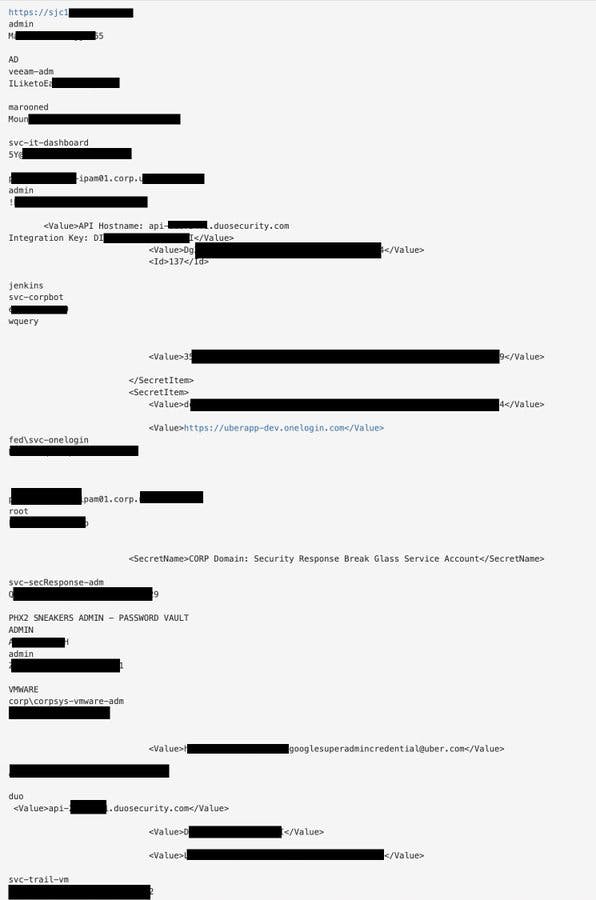
The attacker spammed the employee with push AUTH notification for over an hour and then contacted him on WhatsApp and claimed to be from Uber IT team and told him if he wants it to stop, he must accept the push request. The employee accepted it which led to the hacker adding his device and connecting to Uber VPN where he had access to sensitive data including discovering a network share with PowerShell scripts that included hardcoded security credentials for an admin user. This privilege account manager (PAM) gave the intruder access to extract secrets from all Uber services such as AWS, Google workplace, DA, Petabyte of data Uber stored in google drive, all employee email accounts, security dashboard, financial data all these backed with explicit screenshot and sensitive information.
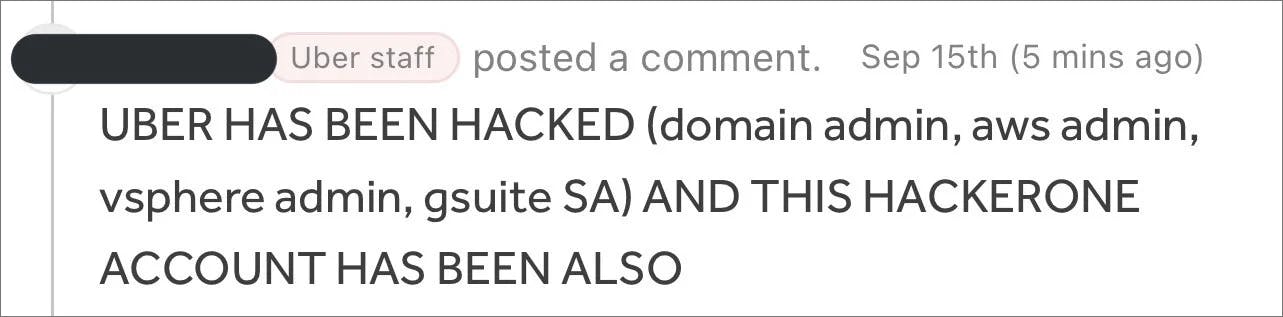
He found Uber slack workspace which he used to eventually announce his presence officially to the company.
Uber response
Since the compromise of the company network resources, Uber has responded by shutting down part of its internal network and staff were told not to use the workplace messaging app “slack” while investigation continues for more incident report and detailed information about the breach.
Implication of the hack
In 2016 Uber was breached and paid the hacker $100,000 to delete information of about 57 million people which also led to the ouster of former chief security officer Joe Sullivan and other executives. Though the matter is still under investigation as tweeted by the company the implication isn’t yet clear but it led to their share price falling by about 6.5% and leaving doubt in the mind of investor about the security architecture of the company. LINK The S&P 500 and Nasdaq composite fell by 1.2 % and 1.6% respectively.
Recommendations:
MFA are activated to ask for OTP or simply accept a push notification button once a suspected activity is noticed on you accessing the site. MFA have recently been falling prey to phishing activity as seen with Twillo. So, what is the way out:
The use of industry standard MFA FIDO2 has proven resistant to these attacks so far.
This breach will lead to many companies’ network having to tighten their internal security system and not just focus on ensuring perimeter are secured.
Social engineering is not new to information security as it has been used even before the innovation of computers. Kevin Mitnick a former infamous hacker used this crude yet effective technique to breach many systems over the telephone by preying on the IQ of susceptible individuals. Today this technique has been sophisticated to include the use of software and scripts that can be bought for some dollars to carry out the attack. Apart from all the security architecture in a network the strongest and weakest links are still humans, companies must continue to carryout awareness and training to their staffs to avoid data breaches.